MailVault: Your Time Capsule for Your Heir or Designated Recipient Ensure Your Crypto Keys Are Delivered—Even After You’re Gone

MailVault
ensures your crypto keys are delivered—even if you're not around. It features a fully E2EE, decentralized mail system for crypto inheritance. Send seed phrases or instructions with timed or trigger-based delivery. Messages stay encrypted and inaccessible until all conditions are met.
“For the final message that matters most.”
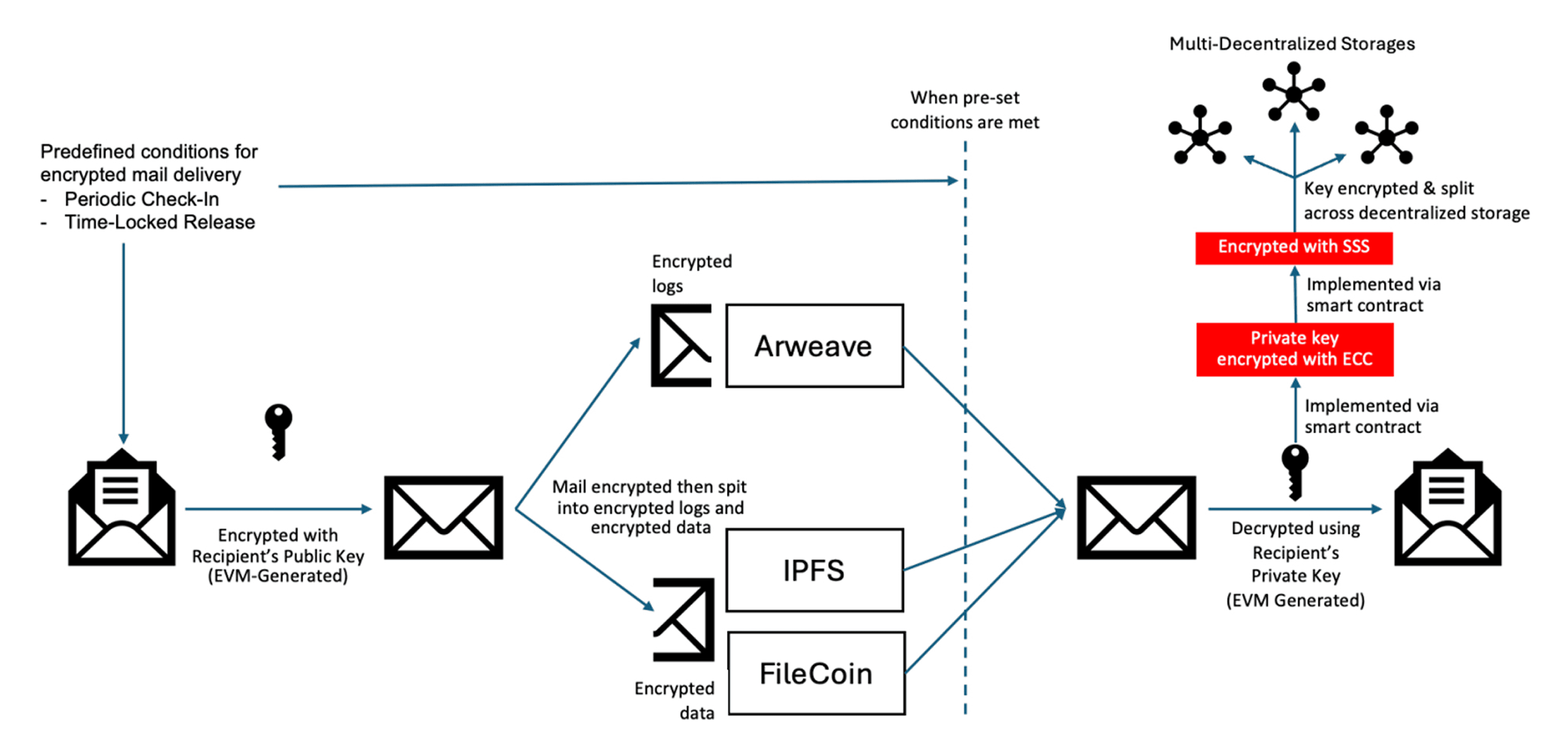
MailVault Flow (Steps 0-4)
Secure, decentralized, and programmable encrypted mail delivery on Purring Spaze.
Step 0: MPC Authentication for Walletless Onboarding
Purpose: Seamless login with secure key generation using Purring Spaze’s native MPC (Multi-Party Computation).
- Users access MailVault using social logins (Google, Facebook, etc.).

- Generates distributed key shares without ever reconstructing the private key.

- Uses threshold cryptography to enable secure operations.

- Empowers the user with a keyless wallet experience to sign, encrypt, and decrypt without managing seed phrases.

🔒 Currently replacing Web3Auth. Upgrade to True MPC (non-reconstructive, zero-trust computation) in development for launch this year.
Step 1: Composing and Encrypting the Mail
Purpose: Send a time-locked or conditionally released message to a recipient.
- The sender composes a mail message and sets predefined release conditions:

- ⏱️ Time-Locked Release: The message can only be unlocked after a set time.

- 🔁 Periodic Check-In: Recipient must prove ongoing activity (e.g., heartbeat pings).

- The mail is encrypted with the recipient’s public key (EVM-generated) so only they can decrypt it.

Step 2: Decentralized Storage of Encrypted Mail
Purpose: Ensure redundancy, censorship resistance, and tamper-proof storage.
- The encrypted mail is split into two parts:

- Encrypted Logs (immutable records) → stored on Arweave

- Encrypted Data (message content) → stored on IPFS and Filecoin

- This architecture prevents single-point failure and supports resilient recovery.

🔐 In case of a breach, attackers cannot decrypt anything without proper cryptographic keys and smart contract approval.
Step 3: Smart Contract Enforcement with Cryptographic Controls
Purpose: Enforce delivery conditions and protect decryption keys.
- Smart contracts handle release logic based on:

- Time-check

- Any other programmable access policy.

- Two encryption layers protect the decryption key:

- 🔐 ECC (Elliptic Curve Cryptography) → encrypts the private decryption key.

- 🧩 Shamir’s Secret Sharing (SSS) → splits the key across decentralized nodes.

- These are deployed and enforced on-chain, with no single party holding the full key.

Step 4: Message Retrieval and Decryption
Purpose: Purpose: Secure delivery and decryption of the message by the intended recipient.
- When all predefined conditions are met:

- Smart contracts reconstruct the decryption key using SSS.

- The encrypted mail is retrieved from decentralized storage.

- It is then decrypted using the recipient’s private key (from their MPC-authenticated wallet).

- The recipient receives the plain-text mail securely — without any centralized party involved.

MailVault Flow Summary Table
| Step | Title | Description |
|---|---|---|
| 0 | MPC Login & Wallet Init | Login via social account → MPC key generation |
| 1 | Compose & Encrypt Mail | Message encrypted with recipient’s public key |
| 2 | Split & Store Encrypted Data | Logs → Arweave, Data → IPFS & Filecoin |
| 3 | Smart Contract Access Control | SSS + ECC enforce time-lock and check-in |
| 4 | Decrypt & Deliver | Recipient decrypts with MPC-based EVM wallet |
Related Articles
Get Started with Crypto Time Capsule
Learn how to set up your first crypto inheritance plan
Set Up Your Wallet Backup
Best practices for crypto wallet backup with public key encryption

Monthly Update: Latest Letter from CEO
Updates on new PurrChat security features and wallet updates
