PurrVault: Your Time Capsule for Yourself or Your Trusted Circle Never Lose Your Crypto Keys Again

PurrVault
Your Time Capsule for Yourself or Your Trusted Circle Never Lose Your Crypto Keys Again PurrVault is a cloud-based, end-to-end encrypted (E2EE), decentralized secure vault designed as a group chat for long-term key storage. Vault owners can create a group, invite members, and generate secret notes with custom access conditions—such as multi-signature approval or a time delay.
Use it with trusted members or your own multiple accounts to create a personal, self-recoverable vault—ensuring secure access to your private keys when needed.
PurrVault Architecture Flow (Steps 0 to 4)
Step 0: Secure MPC Authentication (Keyless Wallet Login)
Goal: Seamless, secure user login and cryptographic key provisioning using Purring Spaze's own MPC engine.
- User logs into Purring Spaze via social identity (e.g., Google, Facebook).

- Behind the scenes, Purring Spaze’s native MPC system:

- Generates cryptographic key shares using multi-party computation.

- Distributes shares across independent nodes — no full private key is ever reconstructed.

- Uses threshold cryptography to allow signing/authorization.

- This creates a keyless wallet experience: users can interact with smart contracts, encrypt/decrypt notes, and sign transactions securely — all without managing a seed phrase.

🔒 Currently replacing Web3Auth. Upgrade to True MPC (non-reconstructive, zero-trust computation) in development for launch this year.
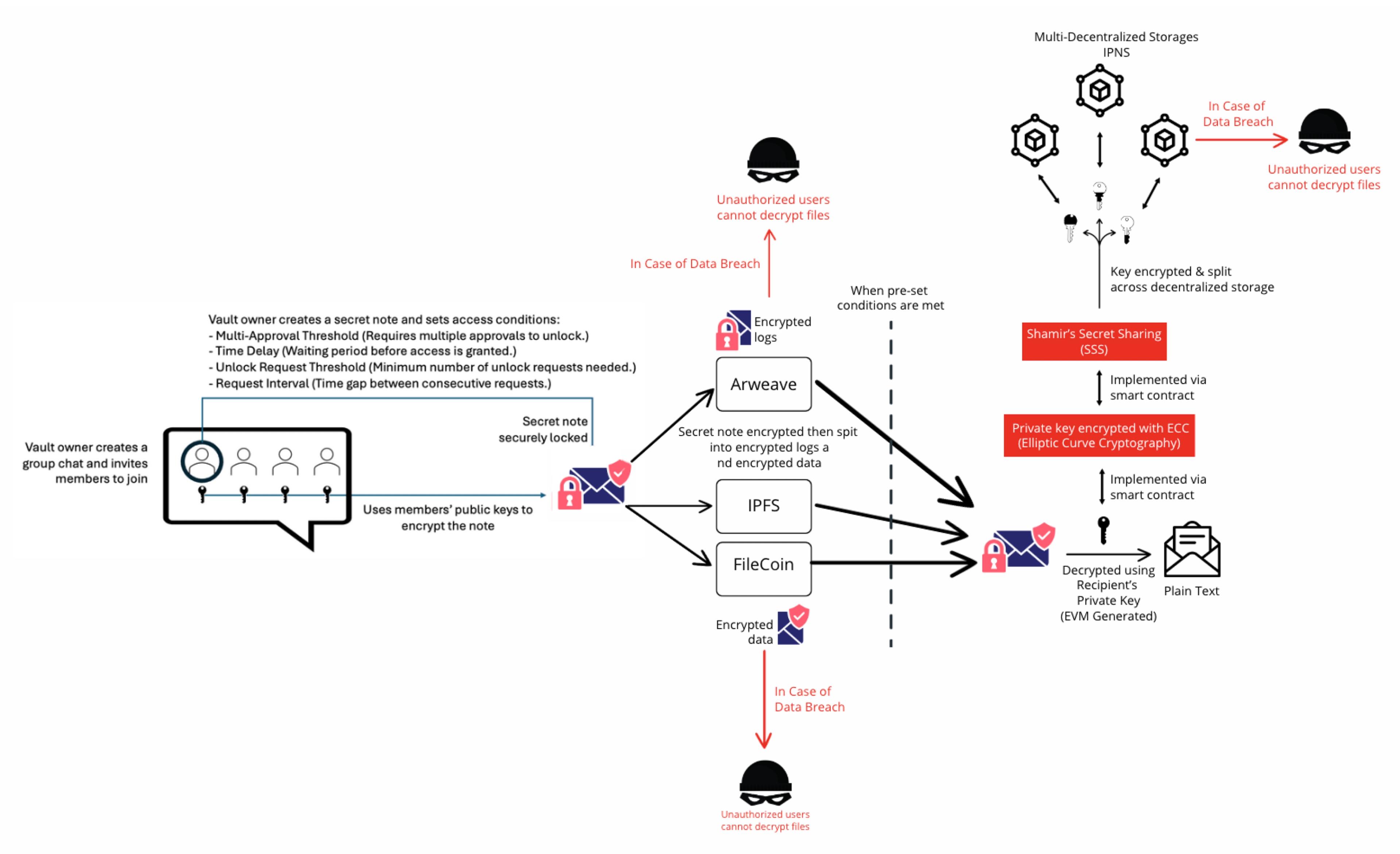
Step 1: Vault Setup & Secret Note Creation
Goal: Vault owner prepares the secure environment for long-term storage and access control.
- The Vault owner creates a group chat and invites trusted members (can also invite their own multiple accounts for self-storage).

- Owner writes a secret note (e.g., seed phrase, private key, message).

- Owner defines custom access conditions:

- 🔑 Multi-Approval Threshold: Require multiple member approvals to unlock.

- ⏳ Time Delay: Wait period before access is granted.

- 📈 Unlock Request Threshold:Minimum unlock requests needed.

- 🕰️ Request Interval: Enforced delay between repeated unlock attempts.

- The note is encrypted using the public keys of group members.

Step 2: Decentralized Encryption & Storage
Goal: Securely store the encrypted note across redundant, censorship-resistant storage systems.
- The encrypted secret note is split into:

- Encrypted logs → immutable record

- Encrypted data → payload of the note

- These are stored across decentralized storage networks:

- 🧱 Arweave (logs)

- 🔗 IPFS

- ⛓️ Filecoin

🔐 In case of data breaches, attackers cannot decrypt the content without satisfying unlock conditions and having the correct key.
Step 3: Smart Contract Logic & Access Enforcement
Goal:Enforce vault access rules in a decentralized, automated way.
- Access attempts are validated on-chain via smart contracts.

- Two core cryptographic mechanisms are implemented:

- 🧩 Shamir’s Secret Sharing (SSS):

- Splits the decryption key among parties or nodes.

- Reconstructs the key only if threshold conditions are met.

- 🔐 ECC (Elliptic Curve Cryptography):

- Used to encrypt the private key securely before distribution.

- Smart contracts ensure that only when access rules are satisfied, the key can be reconstructed.

Step 4: Secure Decryption & Access
Goal:Retrieve and decrypt the secret note securely.
- When unlock conditions are met:

- Smart contract triggers key reconstruction.

- The encrypted data is fetched from decentralized storage.

- The note is decrypted using the recipient's EVM-compatible private key.

- Result: the user receives the plain-text secret (e.g., seed phrase, secret note).

All actions are permissioned, logged, and protected against unauthorized access at every layer — cryptographic, contractual, and infrastructural.
Summary Table
| Step | Title | Core Components |
|---|---|---|
| 0 | MPC Authentication | Native MPC engine, threshold key shares |
| 1 | Vault Creation & Encryption | Group chat, secret note, public key encryption |
| 2 | Decentralized Storage | IPFS, Filecoin, Arweave, encrypted data |
| 3 | Smart Contract Enforcement SSS | ECC, access condition validation |
| 4 | Secure Retrieval & Decryption | EVM-based private key, plain text output |
Related Articles
Get Started with Crypto Time Capsule
Learn how to set up your first crypto inheritance plan
Set Up Your Wallet Backup
Best practices for crypto wallet backup with public key encryption

Monthly Update: Latest Letter from CEO
Updates on new PurrChat security features and wallet updates
